This wiki is locked. Future workgroup activity and specification development must take place at our new wiki. For more information, see this blog post about the new governance model and this post about changes to the website.
TWiki> Main Web>MainOslcCommonArchitecture>ReportingHome>ReportingRESTApi>OAuthenticationTroubles (revision 3)
Main Web>MainOslcCommonArchitecture>ReportingHome>ReportingRESTApi>OAuthenticationTroubles (revision 3)
What is OAuth?
Quoted from http://oauth.net/core/1.0a/The OAuth protocol enables websites or applications (Consumers) to access Protected Resources from a web service (Service Provider) via an API, without requiring Users to disclose their Service Provider credentials to the Consumers. More generally, OAuth creates a freely-implementable and generic methodology for API authentication.
Terminology
* Service Provider - an application that allows access via OAuth.* User - an individual who has an account with the Service Provider.
* Consumer - an application that uses OAuth to access the Service Provider on behalf of the User.
* Protected Resource - data controlled by the Service Provider, which the Consumer can access through authentication.
The Problem
The OAuth protocol describes the details of the communication between the Consumer and the Service Provider but does not define aspects related to the User nor it enforces the authentication protocol used by the Service Provider. The later is not a problem when the User is human but is a major issue for a Software User since there are no mechanisms to programatically determine what protocol is used. So bascially the Software User ends up tyring to use an API which is not known. The manual and programatic workflows are depicted bellow. * Human User - a kid* Software User - the kid's robot
* Service Provider - the kid's grandmother, in charge of the food cabinet
* Consumer - a high tech toaster able to charge itself
* Protected Resource - a loaf of bread
* Service produce - toasted bread
Manual workflow
The human operator knows it is presented with a login screen and identifies the components of the login form.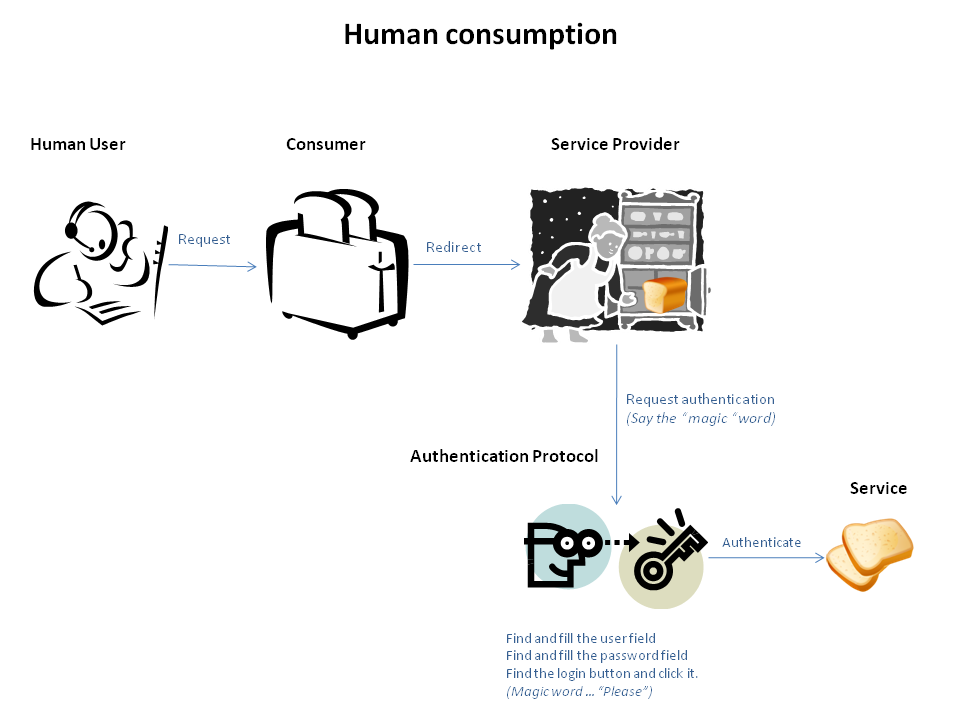
Programatic workflow
The software operator knows it needs to authenticate but has no idea how nor it has the means to "understand" what protocol is used. The authentication protocol used by the service provider can Basic Authentication, Form Authentication or any other protocol. At best, the Software Client can attempt to use a set of known protocols in the hope that one of them will match. In addition some popular authentication protocols such as Form Authentication are not standardised.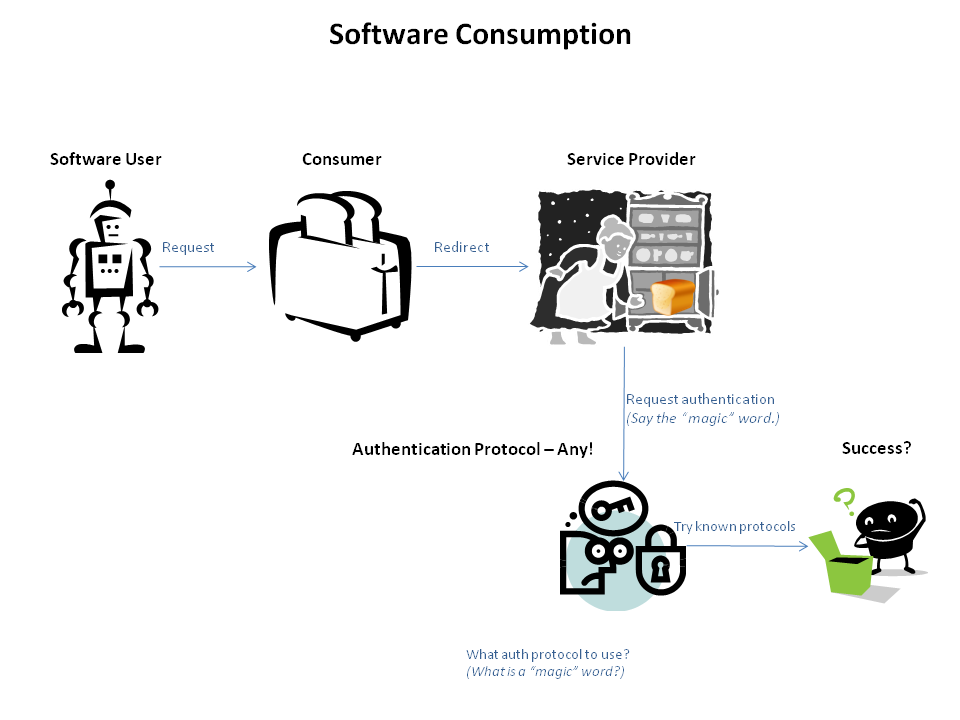
| I | Attachment | Action | Size | Date | Who | Comment |
|---|---|---|---|---|---|---|
| |
human_consumption.png | manage | 58.3 K | 25 Jan 2010 - 12:41 | DragosCojocari | |
| |
software_consumption.png | manage | 49.6 K | 25 Jan 2010 - 12:41 | DragosCojocari |
Topic revision: r3 - 25 Jan 2010 - 15:39:02 - DragosCojocari
Contributions are governed by our Terms of Use
Ideas, requests, problems regarding this site? Send feedback

